Unraveling the Landscape of Cybersecurity: A Comprehensive Guide to Security Breach Map Layouts
Related Articles: Unraveling the Landscape of Cybersecurity: A Comprehensive Guide to Security Breach Map Layouts
Introduction
With great pleasure, we will explore the intriguing topic related to Unraveling the Landscape of Cybersecurity: A Comprehensive Guide to Security Breach Map Layouts. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unraveling the Landscape of Cybersecurity: A Comprehensive Guide to Security Breach Map Layouts
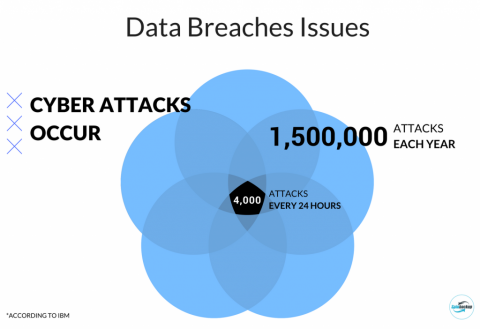
The digital realm, teeming with opportunities, also presents an expansive landscape ripe for cyberattacks. In this interconnected world, where data flows freely and businesses operate across borders, safeguarding sensitive information becomes paramount. Security breaches, unfortunately, are an increasingly common occurrence, leaving organizations vulnerable to financial losses, reputational damage, and legal ramifications. To effectively navigate this complex terrain, a powerful tool emerges: the security breach map layout.
Understanding the Essence of Security Breach Map Layouts
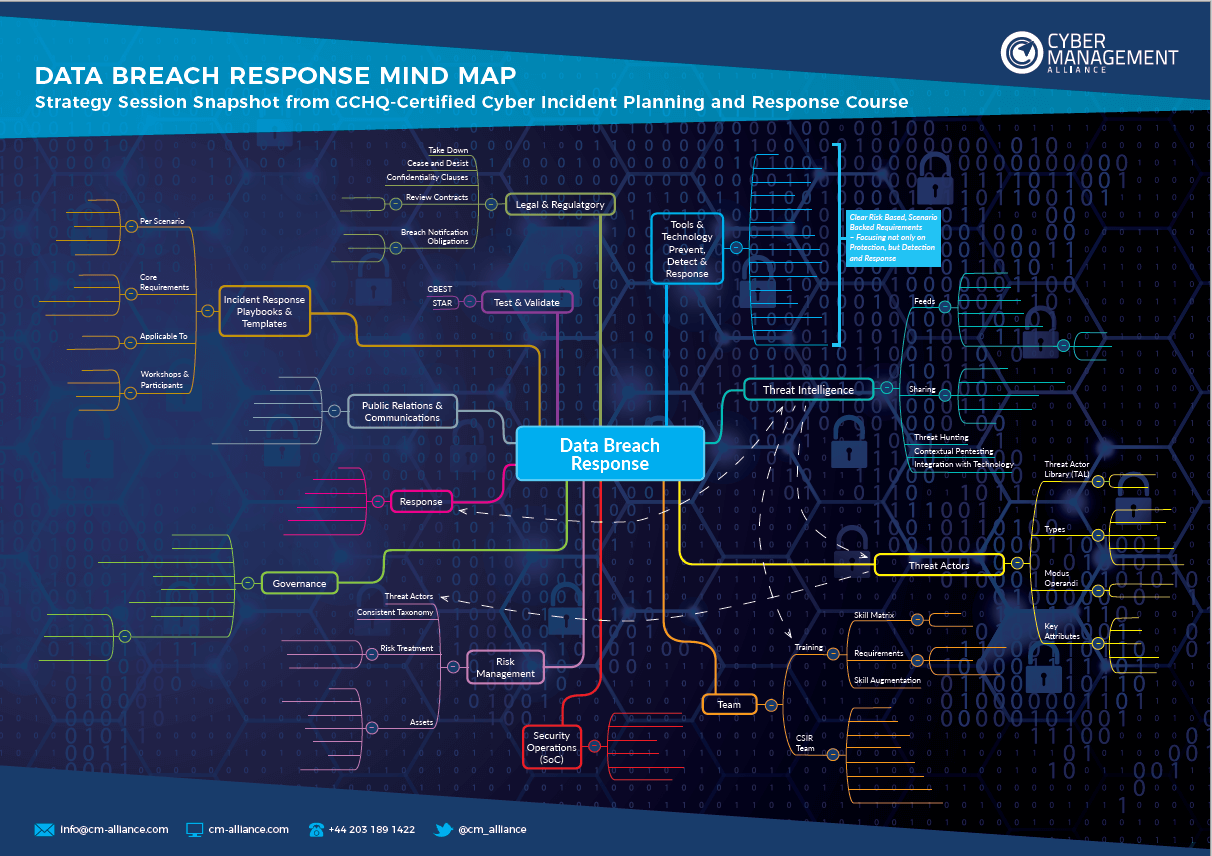
A security breach map layout, at its core, is a visual representation of the chronological sequence of events that transpired during a security breach. It meticulously documents the attack’s progression, highlighting the vulnerabilities exploited, the methods employed by the attackers, and the impact on the organization’s systems and data. This comprehensive visual narrative serves as a powerful instrument for:
- Comprehensive Incident Analysis: The map provides a clear and detailed overview of the attack, enabling security teams to meticulously analyze each stage, identify the root cause of the breach, and understand the attackers’ motives and tactics. This in-depth understanding is crucial for developing effective countermeasures and mitigating future risks.
- Effective Incident Response: The visual representation facilitates efficient communication within the organization. It allows security teams to quickly grasp the situation, coordinate response efforts, and allocate resources effectively. This streamlined approach ensures a swift and decisive response to minimize the damage caused by the breach.
- Enhanced Security Posture: By analyzing the map, organizations gain valuable insights into their security weaknesses and vulnerabilities. This knowledge fuels the development of proactive security measures, strengthening the organization’s overall security posture and preventing future attacks.
- Improved Communication and Collaboration: The map serves as a common ground for security teams, legal counsel, and other stakeholders to understand the intricacies of the breach. This shared understanding fosters effective communication, collaboration, and coordinated efforts in mitigating the incident’s impact.
- Forensic Evidence and Legal Support: The meticulously documented map provides invaluable forensic evidence that can be used in legal proceedings. It demonstrates the organization’s diligence in investigating the breach, strengthens legal arguments, and supports potential claims for insurance coverage.
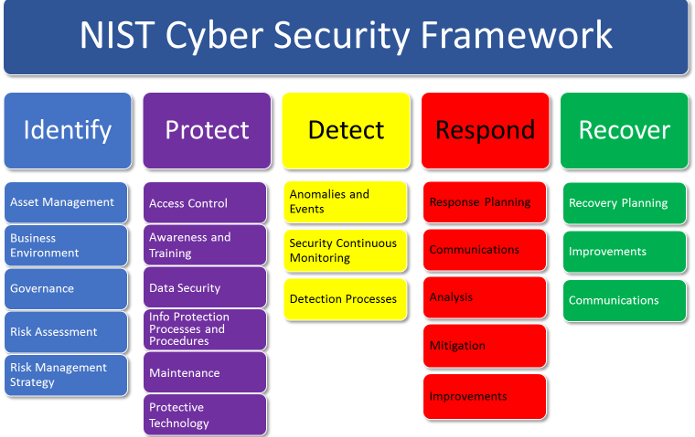
Components of a Robust Security Breach Map Layout
A well-structured security breach map layout encompasses several key components, each playing a vital role in providing a comprehensive picture of the attack:
- Timeline: This component chronologically depicts the sequence of events, from the initial attack vector to the final impact. It clearly illustrates the duration of the attack, the time taken to detect and respond, and the overall timeline of the incident.
- Attack Vectors: This section identifies the specific vulnerabilities exploited by the attackers to gain access to the organization’s systems. It details the methods employed, such as phishing emails, malware, or compromised credentials, providing insights into the attackers’ modus operandi.
- Compromised Systems and Data: This component lists all systems and data that were affected by the breach, including the type of data compromised, the extent of the breach, and the impact on the organization’s operations.
- Attacker Actions: This section meticulously documents the actions taken by the attackers, including the tools and techniques used, the data accessed, and the potential damage inflicted on the organization.
- Response Actions: This component outlines the steps taken by the organization to contain the breach, mitigate the damage, and recover from the incident. It details the actions taken to secure compromised systems, restore data, and notify affected individuals.
- Lessons Learned: This crucial section summarizes the key takeaways from the breach, identifying the vulnerabilities exploited, the weaknesses in the organization’s security posture, and the areas requiring improvement. It forms the basis for developing a more robust security strategy to prevent future attacks.
Types of Security Breach Map Layouts
Security breach map layouts can be tailored to suit the specific needs and complexity of the incident. Some common types include:
- Chronological Map: This layout presents the events in a linear timeline, showcasing the sequence of actions taken by the attackers and the organization’s response. It provides a clear and concise overview of the attack’s progression.
- Flowchart Map: This type of map uses a visual flow diagram to illustrate the attack’s path through the organization’s systems. It highlights the connections between compromised systems, data flow, and the attackers’ movements within the network.
- Hierarchical Map: This layout organizes the information in a hierarchical structure, starting with the initial attack vector and branching out to depict the subsequent actions, compromised systems, and impact. It provides a clear visual representation of the attack’s scope and impact.
- Interactive Map: These maps leverage technology to provide an interactive experience. Users can explore the map, zoom in on specific areas, and access detailed information about each component. This interactive approach enhances understanding and facilitates in-depth analysis.
Benefits of Implementing Security Breach Map Layouts
The implementation of security breach map layouts offers numerous benefits to organizations, including:
- Improved Incident Response: The visual representation of the attack facilitates a faster and more effective response, enabling security teams to quickly identify the attack’s scope, prioritize actions, and allocate resources efficiently.
- Enhanced Security Posture: By analyzing the map, organizations gain valuable insights into their security weaknesses and vulnerabilities, allowing them to strengthen their defenses and prevent future attacks.
- Effective Communication: The map serves as a common ground for communication among security teams, legal counsel, and other stakeholders, ensuring everyone is on the same page and working towards a common goal.
- Improved Compliance and Reporting: The meticulously documented map provides evidence of the organization’s diligence in investigating the breach, facilitating compliance with regulations and supporting legal proceedings.
- Knowledge Sharing and Training: The map serves as a valuable tool for sharing knowledge and training purposes, enabling security teams to learn from past incidents and improve their preparedness for future attacks.
FAQs Regarding Security Breach Map Layouts
Q: What are the key considerations when creating a security breach map layout?
A: When creating a security breach map layout, it is essential to:
- Define the Scope: Clearly define the scope of the map, including the specific attack, the systems and data involved, and the timeframe covered.
- Maintain Accuracy: Ensure the information presented on the map is accurate, reliable, and supported by evidence.
- Clarity and Simplicity: Prioritize clarity and simplicity in the map’s design, using visual aids and concise language to convey the information effectively.
- Customization: Tailor the layout to suit the specific needs and complexity of the incident, incorporating relevant details and focusing on critical aspects.
Q: How can organizations ensure the effectiveness of their security breach map layouts?
A: To ensure the effectiveness of security breach map layouts, organizations should:
- Regularly Review and Update: Regularly review and update the maps to reflect changes in the organization’s security posture, emerging threats, and evolving attack methods.
- Integrate with Incident Response Plans: Integrate the map with the organization’s incident response plans, ensuring it serves as a valuable tool for guiding response actions and communication.
- Utilize Technology: Leverage technology to create interactive and dynamic maps, enhancing user engagement and facilitating in-depth analysis.
- Promote Collaboration: Encourage collaboration among security teams, legal counsel, and other stakeholders in developing and using the maps.
Q: What are some best practices for using security breach map layouts?
A: Best practices for using security breach map layouts include:
- Regularly Review and Update: Regularly review and update the maps to reflect changes in the organization’s security posture, emerging threats, and evolving attack methods.
- Integrate with Incident Response Plans: Integrate the map with the organization’s incident response plans, ensuring it serves as a valuable tool for guiding response actions and communication.
- Utilize Technology: Leverage technology to create interactive and dynamic maps, enhancing user engagement and facilitating in-depth analysis.
- Promote Collaboration: Encourage collaboration among security teams, legal counsel, and other stakeholders in developing and using the maps.
Tips for Creating Effective Security Breach Map Layouts
- Prioritize Clarity and Simplicity: Aim for a clear and concise layout that is easy to understand, avoiding unnecessary complexity or technical jargon.
- Visual Aids and Color Coding: Utilize visual aids, such as icons, symbols, and color coding, to enhance the map’s readability and highlight key information.
- Interactive Elements: Incorporate interactive elements, such as clickable links, zoom functions, and pop-up windows, to provide detailed information and enhance user engagement.
- Regular Updates and Maintenance: Regularly update the maps to reflect changes in the organization’s security posture, emerging threats, and evolving attack methods.
- Training and Education: Provide training and education to security teams and other stakeholders on how to create, interpret, and utilize security breach map layouts effectively.
Conclusion
In the ever-evolving landscape of cybersecurity, security breach map layouts emerge as a powerful tool for navigating the complexities of attacks and bolstering organizational resilience. By providing a comprehensive visual narrative of the attack, these maps enable organizations to analyze incidents, respond effectively, strengthen their security posture, and learn valuable lessons for future prevention. As organizations continue to grapple with the growing threat of cyberattacks, embracing the power of security breach map layouts becomes essential for mitigating risks, protecting sensitive information, and safeguarding the organization’s reputation and future.




Closure
Thus, we hope this article has provided valuable insights into Unraveling the Landscape of Cybersecurity: A Comprehensive Guide to Security Breach Map Layouts. We hope you find this article informative and beneficial. See you in our next article!